By Brad Huallpa
What are computer ports?
Ports act as a docking point for the flow of information between devices in a network. Ports are ordered by their number, which is combined with an IP address to contain a number up to 5 digits long. Digital devices use ports for a variety of tasks, from accessing the Web to sending emails("What is port").
What is port scanning?
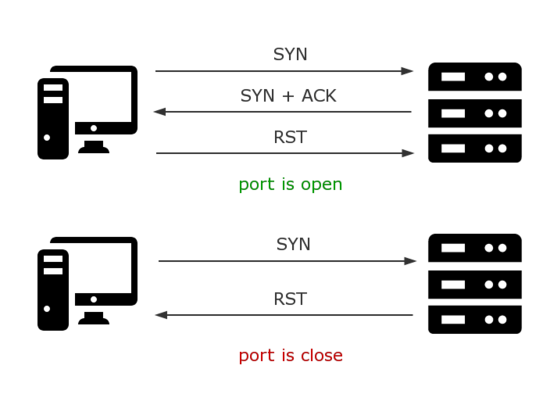
Open ports, which receive and send data, can leave a vulnerability that can be exploited by hackers, to be used for nefarious reasons. To find these ports, hackers use a method called port scanning. Generally, it involves sending packets to different ports and examining the port's reaction to determine vulnerability("What is port").
Two main protocols used in port scanning are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP is characterized as a two-way connection that relies on the destination status. UDP, on the other hand, does not consider the destination status, therefore is considered unreliable compared to TCP("What is port").
Port scanning can be done using a variety of techniques:
What is network scanning?
To begin the process, a hacker must first find an active host. Through a process called host discovery, a network scan is performed to find organizations of IP addresses and hosts. Once the network scan compiles a list of hosts, the port scan determines the open ports that each host has. Network scans can be used by hackers and cybersecurity technicians alike to determine the sensitivity of a network("What is port").
How are ports used to transmit malware?
A common virus planted after port and network scans is botnet malware. Botnet malware infects computers to be controlled remotely by a botnet controller. This controller can command multitudes of bots across multiple infected devices. This communication is done through open ports. A common port used is the Internet Relay Chat (IRC) ports, such as port 6667. IRC ports are used as they require little authentication and have many tools that can be used to conceal identity. Close monitoring of this port and other ports is necessary, as any suspicious behavior can be interpreted as communication between a bot and its commander(Cooke para. 6)
What are ways to stop bot communication in open ports?
One method of exposing bots is to offramp a live network and individually examine each string for known bot commands. However, this is tedious and more sophisticated bots have been found using less common IRC networks. Another method is to study the characteristics of bots, as bots often have a much quicker response time than humans and are dormant most of the time, until enacted by a commander. Ultimately, methods of exposing bots will never succeed in wiping out all the bots, rather just a select few that uses inspected command or control traffic (Cooke para. 48)
What measures can be used to prevent open ports from being infected?
There are many network utilities that can be used to view open ports, and subsequent traffic between users on these ports. One commonly used port for personal computers (PC) is Netstat. Generally, Netstat shows protocol statistics on a network using commands. One such command can allow for listening between ports. An example of a listening command is "sudo netstat -plnt". Upon typing this command, a list of active internet connections will appear. For each network connection, the protocol, the local address, and the foreign address will be show. The local address also contains the name of program identification. Other commands such as "grep" can be used to filter out unnecessary information, which can be useful when trying to pinpoint certain suspicious activity. The presence of suspicious activity can be determined if something other than what is expected is listening to the port. A normally used port will either be silent or have the correct service interacting through it. However, service appearing normal through a port is not complete indicated that it is safe. Further tests must be enacted("Check listening ports").
What Is Port Scanning and How Does It Work?" Avast, 13 Jan. 2021, Retrieved 8 Dec. 2022,"https://www.avast.com/en-us/business/resources/what-is-port-scanning#
Cooke, Evan, et al. The Zombie Roundup: Understanding, Detecting, and Disrupting Botnets. Electrical Engineering and Computer Science Department University of Michigan, Retrieved 8 Dec. 2022, https://www.usenix.org/legacy/publications/library/proceedings/sruti05/prelim_papers/cooke/cooke_html/
Rackspace Support. "Check Listening Ports with Netstat." Support Network, Rackspace US, Inc, 21 June 2012, Retrieved 8 Dec. 2022,https://docs.rackspace.com/support/how-to/checking-listening-ports-with-netstat/